
FFRI,Inc.
1
Monthly Research
Windows New Security Features
- Control Flow Guard
, Inc
http://www.ffri.jp
Ver 1.00.02

FFRI,Inc.
About Control flow guard(Guard CF)
• Control flow guard made its debut at Windows 8.1 Preview release
– It disabled on Windows 8.1 RTM (Release To Manufacturing) and
Windows 8.1 releases
– Available on Windows 10 Technical Preview and Windows 8.1
Update Pack
• We call control flow guard “Guard CF” in this document
– Because acronym of control flow guard(CFG) means control flow
graph generally
2

FFRI,Inc.
Notes
• Guard CF is work-in-progress feature
• We tested Windows 10 Technical Preview and Visual Studio 2015
Preview
3
FFRI,Inc.
Threat Model
• Arbitrary code execution
– Manipulating indirect call operand
• Typical example
– vtable overwrite
4

FFRI,Inc.
Protecting with Guard CF
• Insert check function called before indirect calls at compile time
• The check function validates indirect call target address
– Raises violation if untrusted address’s called
5
…
call check_func
…
call (*myfunc)()
…
…
main():
myfunc1():
shell code
ret
void myfunc1() {
printf("myfunc1\n");
}
int main(int argc, char* argv[])
{
void(*myfunc)();
myfunc = myfunc1;
(*myfunc)();
return 0;
}
Compiler inserts check code
Linker embeds guard information
somewhere:
If the target is trusted function,
calling (*myfunc)()
Exception has occurred
if may call untrusted indirect
call target address
FFRI,Inc.
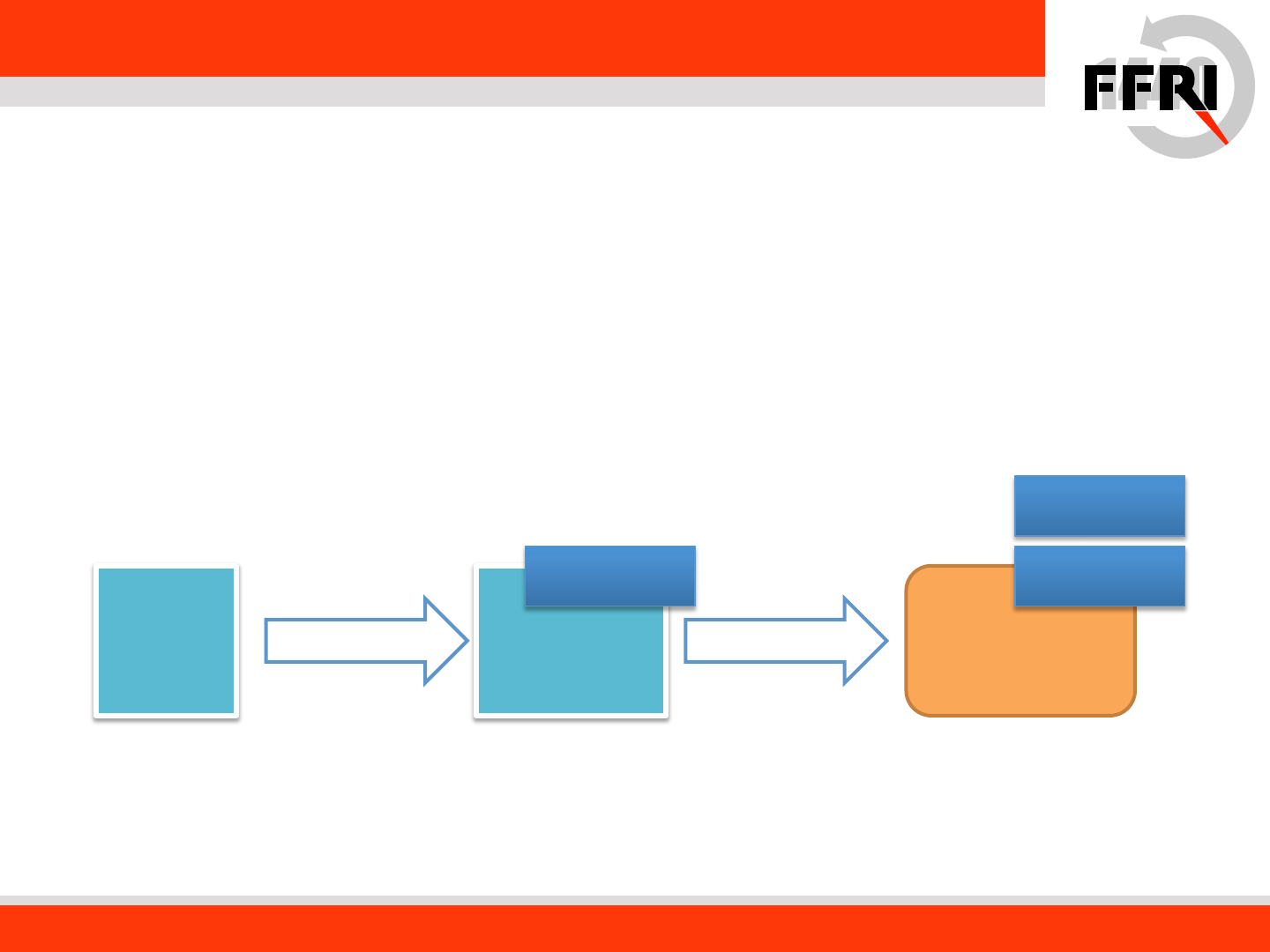
Protecting with Guard CF (cont.)
• Guard CF trusts registered address of guard CF function table
• Guard CF function table exists PE/COFF headers which made by linker
• Windows runtime (ntdll.dll) builds trusted function bitmap from Guard CF
function table at loading time
6
compileCode
Compiler Inserts check
function before indirect calls
Objects Linker
Guard CF
Enabled EXE
Linker makes guard CF configuration
and appends executable file headers
CF Guard
check function
CF Guard
check function
CF Guard
Configurations

FFRI,Inc.
Guard CF in Visual Studio 2015 Preview
• Using hidden option
7
cl /d2guard4 test.cpp /link /guard:cf
See also:
http://blogs.msdn.com/b/vcblog/archive/2014/12/08/visual-
studio-2015-preview-work-in-progress-security-feature.aspx

FFRI,Inc.
PE/COFF headers
• DLL Characteristics
8
OPTIONAL HEADER VALUES
10B magic # (PE32)
…
C140 DLL characteristics
Dynamic base
NX compatible
Guard
Terminal Server Aware
OPTIONAL HEADER VALUES
10B magic # (PE32)
…
8140 DLL characteristics
Dynamic base
NX compatible
Terminal Server Aware
build with guard CF option build without guard CF option

FFRI,Inc.
PE/COFF headers (cont.d)
• Load config structure in PE/COFF headers
9
Sectioncontainsthefollowingloadconfig:
0000005Csize
…
0041D108GuardCFaddressofcheck-functionpointer
00000000Reserved
0041D150GuardCFfunctiontable
2AGuardCFfunctioncount
00003500GuardFlags
CFInstrumented
FIDtablepresent
ProtectdelayloadIAT
DelayloadIATinitsownsection

FFRI,Inc.
PE/COFF headers (cont.d)
10
…
Guard CF Function Table
Address
--------
00401000
00401030
004011E0
00401270
004013F0
…
• Guard CF function table in PE/COFF headers
FFRI,Inc.
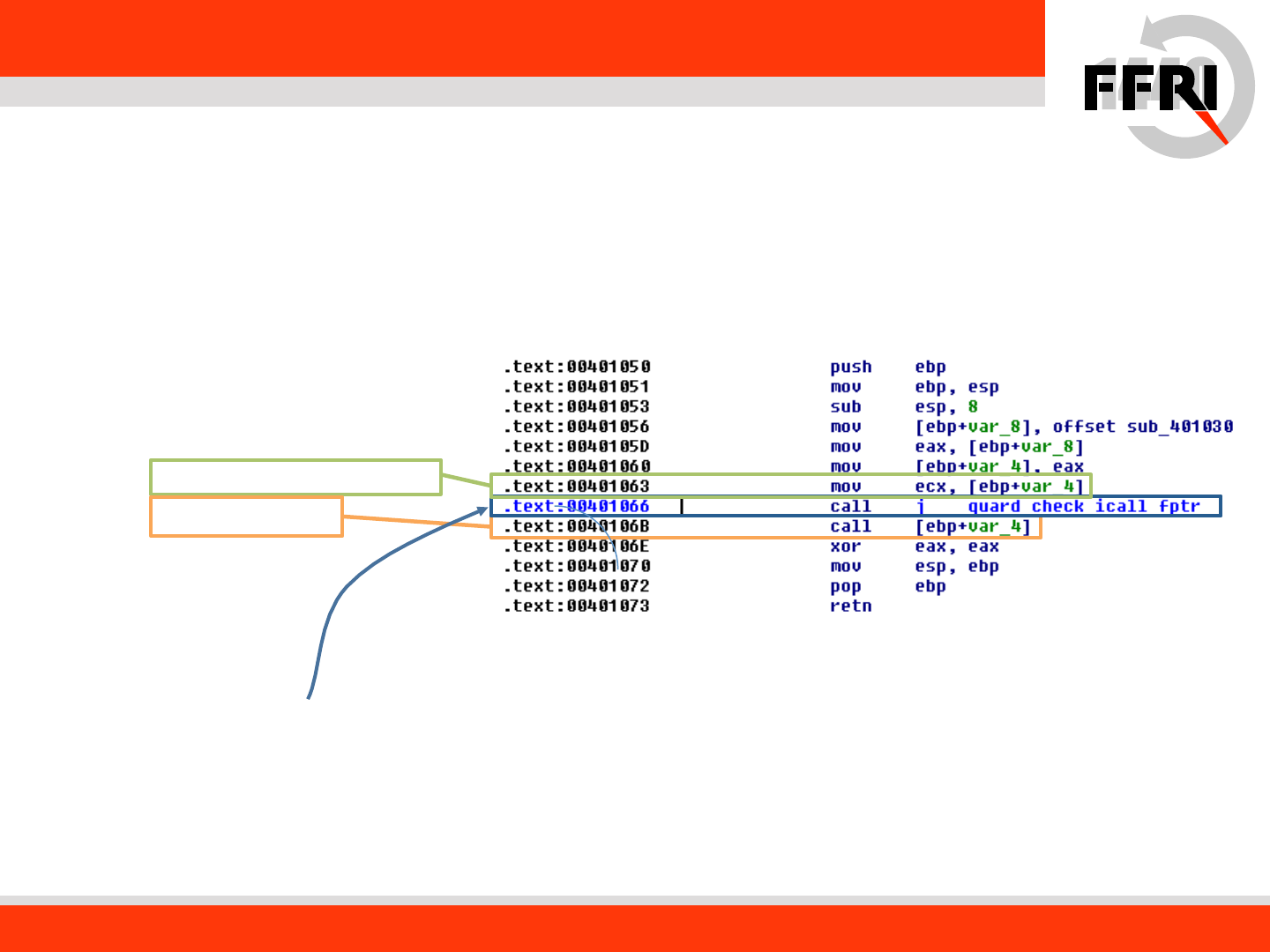
Guard CF Tutorial
11
int main(int argc, char* argv[])
{
void(*myfunc)();
myfunc = myfunc1;
(*myfunc)();
return 0;
}
Inserted Guard CF check function
Dis-assembled view Sample code
FFRI,Inc.
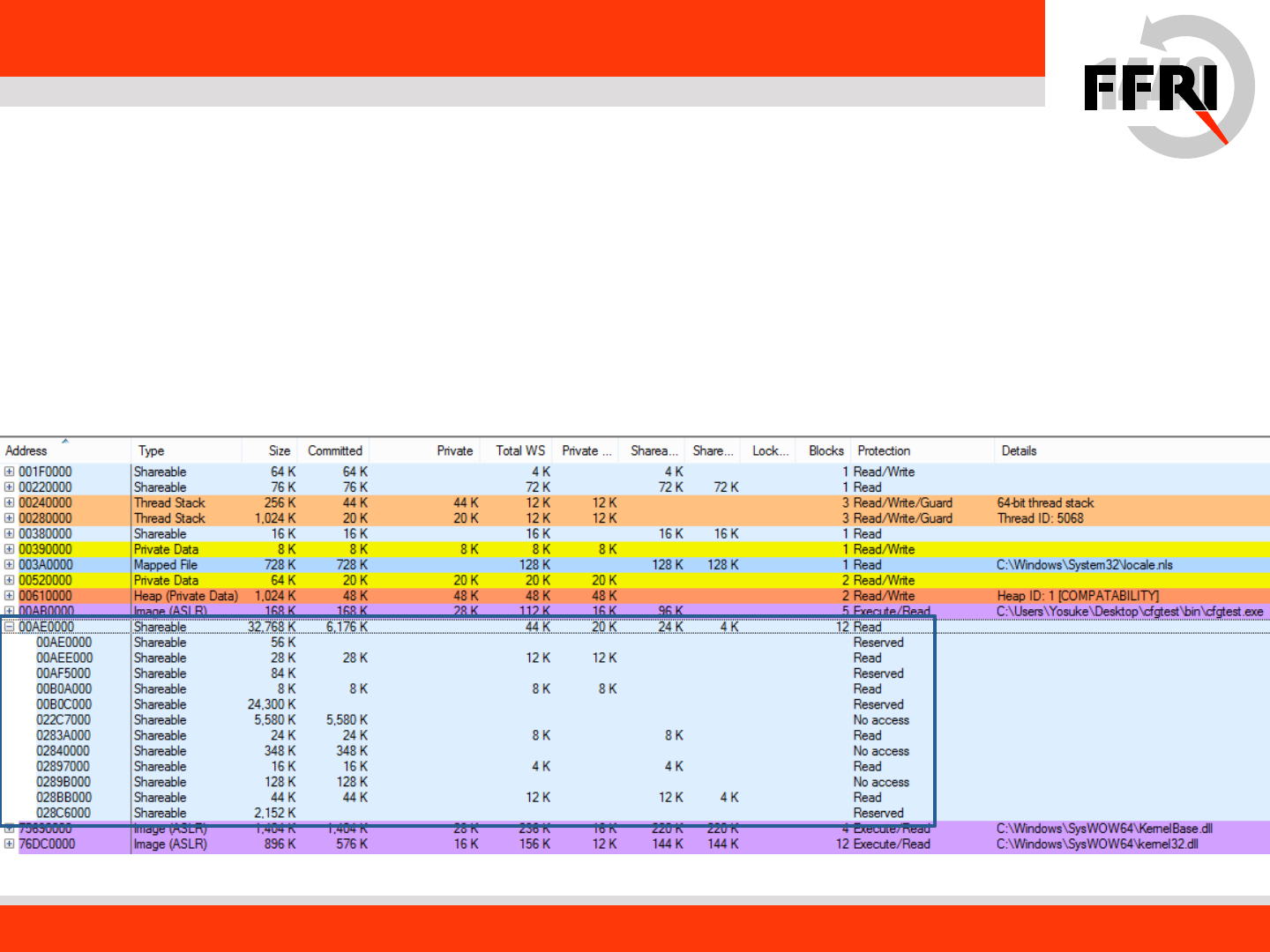
Guard CF Function Bitmap
• Guard CF check function validates target address using bitmap
– Bitmap is created by loader
– Raising security assertion exceptions(int 29h) if call target not
exist in bitmap
12
Allocated bitmap
on process’s
memory
Memory usage (using vmmap)

FFRI,Inc.
Limitation
• CF Guard protects indirect call only
– Indirect jump and return is not protected
• Code reuse attack mitigation is limitedly
– Guarded functions could be called by any indirect caller
13

FFRI,Inc.
Ref: Control flow integrity(CFI)
• Control flow integrity(CFI) restricts indirect branch(jmp, call, ret) source
and destination
– Microsoft researcher published this research in 2005
• CFI implementation uses binary translation and static control flow analysis
14
bool lt(int x, int y) {
return x < y;
}
bool gt(int x, int y) {
return x > y;
}
sort2(int a[ ], int b[ ], int len){
sort( a, len, lt );
sort( b, len, gt );
}
…
…
call sort
…
ret ..
…
…
call ID 17
…
…
…
sort2(): sort():
lt():
gt():
call sort
ID 17
ID 17
ret ID 23
ID 23
ret ID 55
ret ID 23
ID 55
ID 55
CFI inserts ID
and assertion
static control flow analysis
and binary translation

FFRI,Inc.
Relation between Guard CF and CFI
• CFI guaranteed stronger control flow integrity than Guard CF
• But, CFI needs binary translation and many function insertions
– It has an impact on performance and binary compatibility
• Guard CF simplified CFI that checks trustworthiness of call target
15
…
…
call sort
…
…
ret ..
…
call check_func
call [ebp+var_4]
…
…
…
…
…
…
sort2(): sort():
lt():
gt():
call sort
ret
ret
ret
…
bool lt(int x, int y) {
return x < y;
}
bool gt(int x, int y) {
return x > y;
}
sort2(int a[ ], int b[ ], int len){
sort( a, len, lt );
sort( b, len, gt );
}
Inserts check function
at compile time

FFRI,Inc.
Conclusion
• Introducing Control flow guard(Guard CF) design and implementation
– To enable Guard CF for existing source code, application
developers re-compile program using compiler option and linker
option with Guard CF aware compiler
• Microsoft attempting to put Guard CF into practical use
– It based on control flow integrity research over a decade
16

FFRI,Inc.
References
• “Visual Studio 2015 Preview: Work-in-Progress Security Feature”
http://blogs.msdn.com/b/vcblog/archive/2014/12/08/visual-studio-2015-preview-work-
in-progress-security-feature.aspx
(2014/12/19 viewed)
• MJ0011, "Windows 10 Control Flow Guard Internals“, Power of Community 2014.
• Martín Abadi, Mihai Budiu, Úlfar Erlingsson, and Jay Ligatti, “Control-Flow Integrity”,
ACM CCS’05, November 2005
http://research.microsoft.com/apps/pubs/default.aspx?id=64250
17

